The Weaponisation of data.
When I hear the word ‘weaponisation’, I think of the military and war. But data weaponisation not only includes the military, but all areas of our technology lives; business and personal. Today we need to think of data weaponisation as a real war in our lives. It is the new face of war, and we are the targets and the pawns. But let me take a step back for a moment. Let’s look at the traditional view of weaponisation, and at a particular path of what got us here.
The military

Superiority on land 
Superiority in the air 
Superiority on the seas
Traditionally, for most of us, weaponisation has meant military hardware on land, air and sea, and the historical arms race to be based on the accumulation of this hardware. The United States was the winner in this race, and the only super-power as we transitioned into the new millenium.
We then saw other nations develop their nuclear capability, to build their position as powerful nations. This was not only for their standing on the world stage, but also as a deterrent against U.S. aggression and that of their regional adversaries.

20th century atomic bomb 
Ballistic missile launcher 
21st century nuclear bomb
This nuclear arms race extended not only from the U.S., to Russia and some European Union states, but to a bunch of other countries. We suddenly saw countries including India, Pakistan, Iran, North Korea and China enter the nuclear arms race.
The evolution to data weaponisation
In the new millenium, the truly global military mega-powers, in terms of weaponry and nuclear capability, were the U.S., Russia and China. Most of us viewed the others possessing their nuclear capability simply as a deterrent, more than a real global threat.

U.S. Flag 
Russian flag 
Chinese flag
The U.S. kept to the traditional model of military hardware accumulation, while clamping down on the nuclear capability of other nations; however, we saw Russia and China follow a different path.
Realising that they couldn’t outpace or outspend the U.S. in military hardware and nuclear development, we saw Russia and China take an ingenious approach: unconventional warfare and data weaponisation! https://www.brookings.edu/opinions/china-and-russia-vs-america-great-power-revisionism-is-back/
I would be overly exhaustive if I went into the all the areas of trade, economic expansion, foreign aid and geographic expansion, and so I’ll focus on data weaponisation.

A conflicted America 
Russia: The cult of personality. 
China’s geographical trade & foreign aid expansion.
The U.S.
A conflicted America has continued it’s hegemonic approach with a conventional approach to warfare, however constrained by it’s libertarian principles. We hear the voices of liberty and fidelity to the Constitution cry out, whenever America acts along similar parameters to Russia and China’s aggression.
Russia
We have all watched with mouths agape, as Vladimir Putin’s cult of personality has driven Russia’s unconventional warfare. Indeed, his ruthless military aggression against his neighbours, combined with data weaponisation against the world, has left the everyone off-footed. However, Putin is playing by his own rules; by which the libertarian, democratic world cannot compete.
China
If you had told me 20 years ago, that we’d be using the words ‘China’ and ‘superpower’ in the same sentence, I would have looked at you sideways, albeit with a pinch of salt. China’s path to this status came initially through trade, and was then built upon through geographical expansion in foreign aid and technology. Moreover, in their closed and “big brother” society, they have become the experts in data weaponisation.
The data weaponisation war and business disruption come together

Disrupting conventional warfare 
Narrow corporate view of data weaponisation
You must admire the ingenuity of Russia and China. As they realised that they could not take the U.S. head on, they pursued unconventional ways of disrupting the American military machine. We should have known that something was amiss in 2014 when Russian bravado escalated. Do you recall the story of a Russian Su-24 bomber buzzing the USS destroyer Donald Cook within metres, despite U.S. claims that this was pure fake news and propaganda?! Whether fake news, urban legend or whatever, our eyebrows should have risen, when further reports of Russian GPS jamming emerged in 2017. https://www.news.com.au/technology/innovation/military/gps-signals-jammed-norway-finland-warn-pilots-russia-may-blind-their-navigation-systems/news-story/ee28be793012e9b9e66d59ffba439242
However, between 2014 and 2017, there was a lot more happening, that should have given us pause. There was enough Russian chatter that something was afoot in the area of data weaponisation, albeit not fully confirmed. Before we go further, let’s revisit the definition of cyber crime.
Cy·ber crime[sahy-ber-krahym]. Noun: criminal activity or a crime that involves the Internet, a computer system, or computer technology: identity theft, phishing…
Government and the corporate world, had a narrow view at the time of cyber crime. They were focused on hacking, breaching of firewalls, virus injections, online identity theft and ransomware attacks. However, they underestimated the level of sophistication of the attacks.
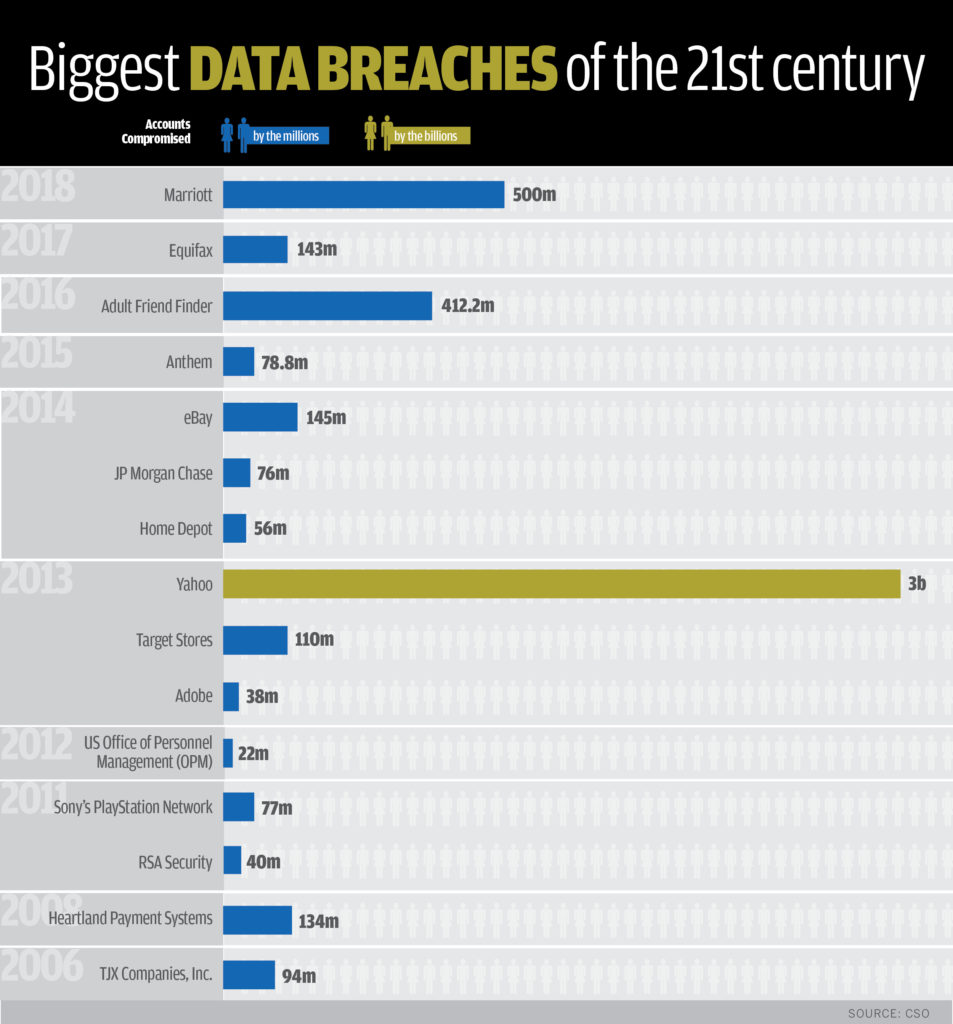
Over the last 10 years, we have woken up to a new age of full-on data attacks that have gone beyond the shadowy-figure cyber crime of old. I find it interesting that 13 of 21 of the biggest data breaches, i.e., a full 62%, were technology companies. They should know better and have better online security and measures to counter such potential breaches! https://qz.com/1480809/the-biggest-data-breaches-of-all-time-ranked/
Full-on data weaponisation

Hooded, shady, young hacker 
Cloak and dagger online breaching
Our mindset was previously of hackers being shady people living in the shadows. In our minds these were either young, errant computer wizkids in their bedrooms, or shady conmen from failing or failed states. In a nutshell, fringe members of society.

Young IT wizard 
Professional hacking 
Young IT sorceress
However, the reality is that hacking and data weaponisation have been professionalised. States like Russia and China, and even North Korea and Middle East countries, have recruited these IT wizards into organised data weaponisation. The Russians hackers have perfected the art and can move from foothold to full-on breach in less than 20 minutes. https://www.wired.com/story/russian-hackers-speed-intrusion-breach/
Even while making it professional, the Russians have carried out their attacks in their inimitable, brutish style. These attacks continue to focus on political organisations like the DNC, political think-tanks, the military and corporate databases.
Political data weaponisation has been the area we’ve been most aware of. We were up in arms over the election breaches and manipulation in Kenya in 2013 and 2017 and in the U.S in 2016. Whether it was Cambridge Analytica, Wikileaks, the Russians or OT Morpho, they used both hacking and data weaponisation to influence these elections. We won’t go into the political aspects of data weaponisation, as the dynamics are unique in that sphere, but focus on the corporate side, which is more relevant to what we are speaking of.
The new sphere of battle

2014 Sony pictures attack 
Identity & Intellectual property theft 
Systems takeover & owner lockout
I believe that rogue nations, along with Russia and China, started getting ideas from North Korea’s alleged hacking of Sony pictures in 2014. As retribution for releasing the movie The Interview, the North Koreans locked Sony employees out of their network and stole all their data. Although the North Koreans didn’t achieve their objective of stopping the release, we saw data weaponisation in the corporate sphere escalating. https://www.usatoday.com/story/news/nation-now/2014/12/18/sony-hack-timeline-interview-north-korea/20601645/
The subsequent attacks focused on techology, pharmaceutical and defence companies, to steal research and intellectual property. In 2018, Russian, Chinese and Iranian hackers targeted more than 45 technology companies and government agencies, and research and intellectual property at more than 144 U.S. universities. https://www.telegraph.co.uk/technology/2018/10/09/china-ahead-russia-biggest-state-sponsor-cyber-attacks-west/
The U.S. is however not sitting idly by. Whether it’s arresting the Huawei CFO, or the ban on ZTE, the U.S. has responded firmly to the Chinese data weaponisation. https://thehill.com/policy/cybersecurity/369848-security-fears-spark-crackdown-on-chinese-tech
https://asia.nikkei.com/Economy/Trade-war/Japanese-suitors-look-past-US-crackdown-on-ZTE-and-Huawei
East versus West online defense mechanisms
Russia and China have put up their virtual “Iron Curtain” and “Great Wall” respectively. We see them use strict government censorship, required government access to corporate networks and strict policing of foreign technology infiltration. They even go as far as developing their own technology platforms, distinct from those of the West, and banning VPNs and social media from the West. I’m not advocating authoritarianism, but…
…organisations in the western world are complacent and reactive. The 2018 Hiscox cyber-readiness survey reported that 72% of companies are unprepared for cyber threats and attacks. In an age when we hear of these threats everyday, that is mind-boggling!
Some suggested defense measures
Companies must take data weaponisation as the greatest threat to their business, both in the micro and macro context in today’s world. Here are a few suggestions.
Cyber security strategy
I believe that every organisation must have a cyber security strategy, endorsed all the way to top leadership. We should adopt the German model where corporate strategies are endorsed up to the Board of Directors level.
Proactivity versus reactive crisis management
Currently there are two models that we see. The predominant “keep our fingers crossed, close our eyes and hope our anti-virus keeps us protected”model, and the visionary online security expert companies who see this as an investment and not just a cost model. The damage from an attack can wipe out the average company, or hobble even the most viable of companies for weeks or months. It’s wiser to be prepared than trying to recover and learn from an attack.
Dedicated IT security budgets
Most organisations invest less than 10% of their IT budgets – not total budget, but IT budget – on online security. The Gartner Research and Advisory Company estimates the average cost of a cyber attack to be US$ 5 million, and the Ponemon Institute breaks it down as follows.
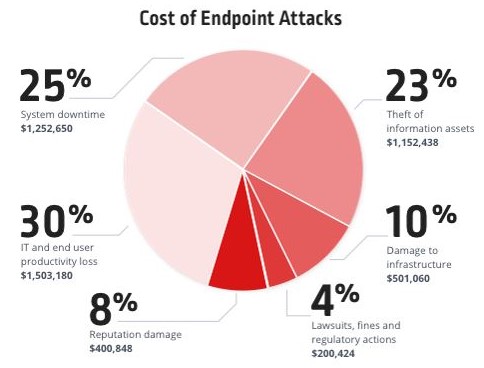
However, with examples of larger cyber attacks like the WannaCry virus and Equifax breach, each at US$ 4 billion, and cyber crime annual damage expected to hit US$ 6 trillion by 2021, having strategic and task-based IT & network security budgets is essential. https://www.varonis.com/blog/cybersecurity-statistics/
Beyond anti-virus
Anti-virus protection defends against attacks from sources such as file-based intrusions and viruses of known configuration. However, hackers can identify weaknesses in the leading anti-virus softwares and target these. We, as safety-conscious and responsible corporate citizens must put up additional lines of defense such as firewalls, intrusion detection and protection systems, encryption, biometric identification and network defense system testing.

Existing biometric 
Evolving biometrics
Back-up & Recovery
Back-ups, back-ups, back-ups! It will save you money, time, stress and heartache, to have data securely backed up and recoverable, rather than have to reconstruct hacked/ stolen data. The heartache of reconstituting hacked data is bad enough, and it will also save the productivity and downtime costs of a cyber attack.
When will it end?
As we evolve from big data to apps and from on-premise to cloud, we’ll have more IT/ network security options in future. Just like the cold war, it will quickly become a choice of either destroying each other or learning to get along. I believe common sense and instincts of self-preservation will prevail. Or…if we don’t get wise to data weaponisation, China will achieve world domination and simply become the sole super power.
Follow on: